
Emerging technologies are often met with skepticism and a degree of caution, and the Exploit Prediction Scoring System (EPSS) is no exception. As a tool for evaluating Common Vulnerabilities and Exposures (CVE) exploitability, EPSS has attracted praise, criticism, and response to criticism. However, while EPSS is still climbing its hype cycle, it is worth our collective attention and evaluation.
In this post, we will explore the practical role of EPSS in prioritizing vulnerabilities, compare EPSS vs. CVSS – Common Vulnerability Scoring System), and explore how EPSS fits into a more comprehensive vulnerability management framework.
The Exploit Prediction Scoring System (EPSS) was created by the Forum of Incident Response and Security Teams (FIRST) and first presented in Blackhat 2019. To quote the formal EPSS website:
The Exploit Prediction Scoring System (EPSS) is an open, data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild.
…
The EPSS model produces a probability score between 0 and 1 (0 and 100%). The higher the score, the greater the probability that a vulnerability will be exploited.
EPSS is often mentioned in the same breath as Common Vulnerability Scoring System (CVSS). Again, the formal CVSS web page (also maintained by FIRST) describes it the best:
The Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity. The numerical score can then be translated into a qualitative representation (such as low, medium, high, and critical) to help organizations properly assess and prioritize their vulnerability management processes.
Thus, both EPSS and CVSS are maintained and developed by FIRST, with the common goal of assisting organizations in prioritizing vulnerability remediation efforts to tackle potential vulnerabilities. The question then arises: which one should you use?
There are two universally correct answers that may both be cliché, but are also accurate in this situation:
To understand the performance of EPSS vs. CVSS, the researchers from the Blackhat paper (Jay Jacobs, et al.) computed metrics such as true positive rate (TPR), false positive rate (FPR), efficiency (precision), and coverage (recall) for both systems using a sample dataset. These metrics help evaluate how well each system identifies and prioritizes vulnerabilities.
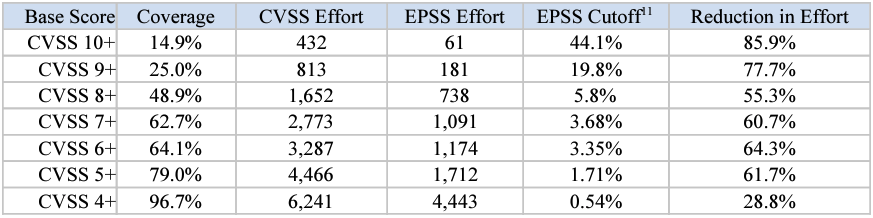
The results showed that EPSS theoretically outperforms CVSS in terms of reduction in effort as can be seen in this diagram (Jay Jacobs, et al., Table 5, page 14). This is especially significant for vulnerabilities with a base CVSS above 9.0.
Nevertheless, it is important to acknowledge that EPSS, by itself, should not be regarded as a comprehensive solution to address all vulnerability prioritization challenges, nor does it claim to be one.
Prioritizing vulnerabilities can be visualized as a funnel, where each step helps focus on what needs to be addressed. The process involves the following steps:

EPSS, KEV, and similar sources provide valuable insights into the exploitability of vulnerabilities. However, they should not be relied upon as the sole source of information. It provides insight into half of the equation for risk (likelihood), while the other half (impact) requires a business impact analysis.
By using EPSS, KEV, and CVSS as part of a more comprehensive vulnerability management approach, organizations can benefit from its insights while considering other aspects such as business context, exploitability, and fixability. This integrated approach allows for better prioritization of resources and efforts to address vulnerabilities.
EPSS, though still an emerging technology, is a valuable tool in the toolbox of organizations looking to prioritize vulnerabilities. It should be used in conjunction with other vulnerability management techniques, considering factors such as business impact, exploitability, and the availability of fixes. By adopting a comprehensive approach to vulnerability prioritization, organizations can make better-informed decisions and distribute resources more effectively to protect their systems and data from potential threats.